The darknet, also known as the dark web, is a concealed section of the internet that's inaccessible via standard search engines. You can only access it using special software, settings, or authorization. This area comprises websites and content that are purposely kept hidden from public view.
Accessing darknet requires using Tor Browser, a special web browser that routes your internet traffic through a global network of relays managed by volunteers. This way, it becomes very difficult to trace which websites you're visiting, and these sites won't know where you are located.
When visiting the dark web, use a secure browser like Tor, do not reveal any of your personal information, and don't open suspicious files or links to stay safe.
The Darknet is often utilized for secure communication, discreet information or file sharing, anonymous research without identity exposure, and occasionally for engaging in illicit activities. It is also recognized for hosting underground black markets(darknet markets), whistleblowing platforms, and discussion boards that champion freedom of speech.
While accessing Darknet Markets themselves is typically not against the law in most places, engaging with illicit goods within them is generally considered a crime. On the other hand, some people might visit Darknet Markets for lawful purposes such as research, journalistic work, or simply to explore online communities. It's essential to know the local laws regarding online activities, and be cautious when using these platforms to avoid any potential issues.
Guide on VeraCrypt Hidden Volumes & Compartmentalized Identities
VeraCrypt is free, open-source disk encryption for people who care about privacy. It creates encrypted “containers” that look like one ordinary file to the OS, but inside can hold drives’ worth of data locked by strong cryptography. If someone copies your container, all they see is random noise, no filenames, no folder tree, no hint anything’s hidden. Without the password, breaking in isn’t realistic today.
Where it gets interesting is the hidden volume feature. This isn’t just password-protected storage, it’s built for plausible deniability. One container can hold two separate volumes, each with its own password. One password opens an outer “decoy” with harmless files you’re fine showing; the other opens the real data stored in unused space. The whole file is random, so there’s no technical proof a second volume exists. Deniability usually fails from behavior or system traces, not from the cryptography.
If you might be coerced to unlock files, whether by an abuser, a corrupt official or aggressive local laws, this lets you reveal something plausible while keeping the real content safe. Used correctly, hidden storage is an OPSEC layer that protects you when normal encryption isn’t enough. It won’t save you if you leave traces elsewhere or talk about what’s inside.
A hidden volume gives you two passwords in one file. The container looks like random data either way. If you’re forced to unlock something, you can reveal the decoy and keep the hidden data safe, as long as you follow this workflow.
Preparing for deniability
Run the host OS in live mode and wipe RAM at shutdown to avoid any leftover traces.
Store your hidden VeraCrypt container on an external HDD (not on the internal drive). SSDs can leak hidden volume info via TRIM or metadata.
Plan for emergencies: have a hotkey combo and script that instantly shuts down the system and wipes RAM. Typically you press a key to leave the VM (e.g. right Alt) then another (e.g. right Ctrl) to run the emergency script.
These steps ensure no forensic evidence remains that could reveal the existence of the hidden volume; an adversary sees only the decoy if you reveal that password.
Why this is good for OPSEC
Plausible deniability, the file has no markers that prove a hidden volume exists.
One file, two stories: show harmless content without exposing sensitive data.
Small forensic footprint when used correctly.
Portable across Windows, macOS and Linux.
Defense in depth: strong cryptography plus decoy strategy plus system hygiene.
Hidden volumes aren’t magic
If you sloppy-mount, write to the outer without protection, let your OS leak recent files, or you live where key disclosure is legal, deniability can fail. Treat this as one layer, not the only layer.
What you need
VeraCrypt installed.
Windows: installer is enough.
macOS: install macFUSE first, then VeraCrypt.
Linux: use your package manager or the official tarball.
A believable decoy idea.
A location for the container file, for example ~/Documents/Archive.dat.
1) Create the outer volume
1. Open VeraCrypt choose Create Volume, then Create an encrypted file container.
2. Choose Standard VeraCrypt volume.
3. Select File, pick a normal name, for example VacationPhotos.dat. Avoid sketchy paths.
4. Encryption options: defaults (AES and SHA-512) are fine. Security outweighs speed here, so layer multiple encryption algorithms, starting with AES. For example, stack AES with Twofish or Serpent for additional security, even if it slows things down.
5. Volume size: pick something that fits both decoy and hidden later. Example: 40 GB total if you plan 6 GB for decoy and about 20 GB for hidden with headroom.
6. Set the outer password. Make it long and different from your hidden one. Skip a keyfile for the outer to keep the story simple.
7. Filesystem:
Windows only: NTFS
Cross-platform: exFAT
Linux only: ext4
8. Click Format. VeraCrypt fills with random data, which enables deniability.
2) Build a believable decoy
Mount the outer volume with the outer password.
Add harmless files that fit your profile (ebooks, school PDFs, screenshots, photos).
Open and edit a few so timestamps look natural.
Don’t fill it; leave space for the hidden volume and later edits.
Dismount.
3) Create the hidden volume
1. Create Volume again, choose Hidden VeraCrypt volume, Normal mode.
2. Select the same container file you made for the outer.
3. VeraCrypt scans free space and suggests a size. Pick a size that fits your real data and leaves free space for outer edits. If the outer is 40 GB with 32 GB free, set hidden to about 20-24 GB.
4. Set a different, stronger hidden password. You can add a keyfile only if you can keep that story straight.
5. Choose filesystem and Format.
6. Done: two volumes in one file.
Opening the hidden volume
Mount, enter the hidden password, work, then dismount.
In Preferences enable wiping cached passwords on exit.
Set a hotkey to dismount fast.
Opening the outer without damaging the hidden
Mount with the outer password.
When prompted, choose protect hidden volume against damage.
Enter the hidden password so VeraCrypt can block overlapping writes.
Make occasional harmless edits in the outer volume to keep the decoy alive.
Keep the decoy believable
Open it sometimes and save a note or tweak a doc.
Don’t keep only archives; include loose files and folders.
Match filenames to contents: if it says Photos, include some photos.
System hygiene that actually matters
Windows
Disable hibernation, powercfg /h off.
Clear pagefile at shutdown, set ClearPageFileAtShutdown=1, or use Group Policy.
Turn off indexing for the mount point: right-click the mounted drive, Properties, uncheck indexing.
Enable auto-dismount on logoff or power saving in VeraCrypt.
macOS
Exclude the mount point from Spotlight, mdutil -i off /Volumes/YourMount.
Avoid Quick Look on sensitive files to limit thumbnail writes.
Use FileVault so swap and temp files are encrypted at rest.
Linux
Use encrypted swap, or disable swap while working with sensitive files.
Mount with noatime if you care about access‑time writes.
Prefer an encrypted home for where the container lives so temp files and thumbnails are covered.
All platforms
Don’t let cloud sync touch the container while mounted. Only sync the closed file if you accept size and modified-time metadata exposure.
Name the file something boring and place it somewhere boring.
Back up the closed container and protect the backup with the same OPSEC.
Key choices that influence deniability
Passwords: the outer should be strong but believable; the hidden should be very strong.
Keyfiles can help but complicate your story. If you use one for hidden, store it somewhere natural and never mention it.
Sizes: don’t make the hidden area consume all remaining space. Leave slack so the outer can still be used.
Container vs partition: files are easier to explain; partitions can be cleaner on Linux. Pick what matches your profile.
Common mistakes that break the model
Writing to the outer without enabling protect hidden volume.
Letting your OS leak file paths in recents, thumbnails, office histories.
A decoy with zero edits for months looks abandoned.
A weird path or suspicious filename for the container.
Talking about the setup; plausibility dies when the story leaks.
Threat model notes
Coercion and key-disclosure laws: some countries can compel decryption. Hidden volumes help only if you can reveal one password and decline the other. Know your local law.
Live response capture: if the system is seized while mounted, deniability is gone. Dismount when idle, use hotkeys, lock the screen.
Forensic side channels: the container looks random, which is normal, but your system can still hold traces. The hygiene list above isn’t optional.
Quick checklist
Outer created, decoy loaded, believable.
Hidden created, different strong password.
Protect hidden volume every time you mount the outer.
Hibernation and swap handled.
Spotlight or indexing disabled on the mount point.
Recents and thumbnails managed.
Backup plan for the closed container, offsite if needed.
Frequent dismounts, cache wipe on exit.
FAQ
Can someone prove a hidden volume exists?
No, not from the container alone. It looks random either way. Failures come from behavior or system traces.
Does SSD TRIM ruin this?
For a file container on a normal filesystem, the container still looks random. TRIM at the disk level doesn’t reveal the hidden area inside. For full-disk or partition encryption, read the docs and decide.
Is a hidden OS worth it?
Windows only; adds complexity. Most people are better served by a clean host plus containers.
Advanced tips that cut noise
Use fixed mount points per OS; predictable paths are easier to purge from recents.
Prefer one big container over many tiny ones. If you need multiple identities, map each identity to its own container.
Keep filenames boring (Archive.dat, MediaCache.bin). Rename only when closed.
If you sync the closed container, hash it first for backup verification—for example shasum -a 256 on macOS, sha256sum on Linux, certutil -hashfile on Windows.
For cross‑platform use, exFAT is fine. Journaling adds write churn; only use it if needed.
Backups without leaking context
Back up the closed file only, never the mounted contents.
Store a second copy on a drive that’s also encrypted at rest (FileVault, BitLocker, LUKS).
Keep versioning simple: date suffix or short counter, for example Archive-2025-09-08.vc or Archive-v03.vc.
Test restores on an offline machine; confirm both outer and hidden passwords work.
Operational habits that save you
Mount only when working; dismount when you step away.
Auto-dismount on screensaver and sleep; wipe cached passwords on exit.
Keep a tiny desk note, “Mount outer with protection.” It prevents the most common mistake.
Run a monthly hygiene day: clear recents, Quick Look, Office MRUs, thumbnail caches, and verify your backup hash.
Troubleshooting quick hits
Outer refuses protection? Be sure you enter the hidden password at the prompt. If you changed the hidden size, you may need to recreate the outer.
A “corrupt” container? Try mounting read-only. If it mounts, copy data out and rebuild fresh containers.
Missing space inside the outer? You likely filled near the hidden boundary. Move or delete decoy files, then try again with protection enabled.
Templates you can copy
Outer filenames
Archive.dat
SystemCache.bin
PhotoLib.idx
MediaStore.cache
Decoy folders
Books, PDFs, Receipts, Photos, School, Taxes, Manuals
Compartmentalization, split identities, accounts, and devices
Treat each identity like a clean room. Each gets its own storage, browser, email, 2FA, network path and habits. No cross-links, no shared recovery, no shared devices if you can avoid it.
The identity bundle model
For each identity assign:
Storage: one VeraCrypt container per identity. Name and size should match the cover story.
Email: one mailbox per identity, no shared recovery addresses, no phone reuse across identities.
Password vault: either one separate vault file per identity, or a single vault with strict per-identity tags plus exportable subsets. Separate vault files are cleaner.
2FA: one or more FIDO keys dedicated to that identity, plus optional TOTP. Don’t store TOTP seed QR images inside the same container that holds the accounts they protect.
Browser: one profile per identity at minimum. Better, one OS user per identity. Best, one VM per identity. On Qubes, one AppVM per identity is ideal.
Network path: pick Tor or a specific VPN provider and exit region for that identity and stick to it. Avoid reusing the same egress for multiple identities in the same session.
Time zone and cadence: use consistent login windows and time zone hints for each identity.
Minimal setups by platform
Windows
One local Windows account per identity each with its own container and browser. Use different default downloads and wallpapers to avoid slips.
Label FIDO keys with tiny marks only you understand.
macOS
Make separate macOS users for higher-risk identities. If staying in one user, split browser profiles and use separate mount points (for example, /Volumes/ID1 and /Volumes/ID2).
Exclude each mount point from Spotlight and Quick Look.
Linux
Separate UNIX users or containers (systemd-nspawn, LXC or full VMs). Use noatime on identity mount points.
On Qubes, give each identity its own AppVM and container. Use a distinct NetVM per identity.
Email and recovery hygiene
Never reuse recovery emails between identities. Recovery links are the most common cross-leak.
Avoid phone recovery reuse. If a number is tied to one identity, park it there permanently and don’t share it.
Aliases are fine within one identity; don’t cross identities. Keep aliases grouped.
Turn off importers that sync contacts and calendars across accounts. Those create background links you didn’t intend.
Password and 2FA flow
Use one long passphrase per identity for the container, and a different one for the vault inside.
Register two hardware security keys per critical identity: one daily key and one sealed backup stored elsewhere.
If you use TOTP, keep the authenticator on a separate device. Export encrypted TOTP backups to a different container that isn’t mounted at the same time.
Document which services support hardware keys versus TOTP in a small text file inside the identity’s container. Keep it boring, something like “Accounts.txt.”
Browser and app isolation
One browser per identity; change theme and search engine to reduce muscle-memory slips.
Turn off browser password save; rely on the vault. This reduces autofill crossing identities.
Clear “Open Recent” in editors after each session, or run portable apps inside the mounted container so recents live there and not on the host.
Network separation
Pick a consistent network path per identity; for example, Identity A uses Tor only and Identity B uses VPN Provider X via country Y. Don’t change paths mid-session.
Use different DNS servers or force all traffic through your chosen tunnel. Run leak checks at the beginning of each session.
If you’re on Qubes, keep your VeraCrypt container in its own vault VM with no network connection. Use Qubes clipboard and file transfer features to move data between this vault and your working AppVMs. For working VMs, assign a separate netVM for each identity.
On conventional systems, use a separate VM per identity and run the VPN client inside that VM.
Content and stylometry
Reuse templates carefully; small style tells add up. Vary punctuation, emoji, greeting lines and posting cadence per identity.
Never paste raw text between identities without a scrub; whitespace and hidden characters can identify an editor or OS.
Strip EXIF from images before they touch any identity. Keep your EXIF tools inside each identity’s container so logs and configs don’t cross.
Example identity matrix
Below is a compact table showing how you might organize three identities. The letters refer to the identity row; you don’t need to repeat them in the Browser or Network columns.
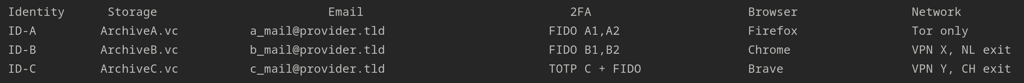
Daily session playbook
Boot the right user or VM.
Mount the right container, confirm the mount path.
Open the vault, unlock the browser, verify the network path.
Work. Don’t mount or use another identity in the same window.
Close apps, clear recents if needed, dismount, verify the container timestamp changed if you saved.
Switch identities only after a cooldown with a fresh network path.
Red flags that mean rotate
You reused a recovery email or phone number.
Two identities logged in from the same browser or device minutes apart.
You copied files between containers without scrubbing.
You revealed details about the hidden setup; rebuild with a different story and structure.
Quarterly audit checklist
Verify backup hashes for each container.
Rotate at least one password per identity; start with the vault master.
Re-register your backup FIDO key on critical accounts and confirm both keys still work.
Test restores offline: mount both outer and hidden.
Review browser profiles; clear or rebuild if they collected residue.
Bottom line
Hidden volumes protect data under pressure. Compartmentalization stops identities bleeding into each other. Pair them: one container per identity, one browser per identity, one network path per identity. Keep the story boring, the workflow consistent and cleanup regular. That’s how good cryptography turns into real privacy.
